Highlights:
- Security tabletop exercises help identify cybersecurity blind spots before cybercriminals can exploit them.
- Tailor your cybersecurity exercise to participants’ expertise, using detailed scenarios for experts and high-level approaches for others.
Cybersecurity preparedness isn’t achieved overnight—it demands ongoing A/B testing to effectively combat the ever-evolving smart attacks of today.
Every organization must have a technology or platform in place that tells how well your organization will respond to an attack and provides cybersecurity insights for overall development. Cybersecurity tabletop exercise can be helpful in this scenario.
It simulates security scenarios to test team responses, helping organizations, governments, and the military to prepare for crises like cyberattacks.
Importance of Cybersecurity Tabletop Exercise: 5 Key Areas that Boosts Cybersecurity Preparedness
Cybersecurity tabletop exercises are essential for organizations to practice responding to cyber threats in a controlled environment.
They assist to identify vulnerabilities, improve communication, and refine response strategies, ensuring better preparedness for real-world attacks.
As cyber threats evolve, these exercises are key to strengthening an organization’s security posture. It includes:
- Vulnerability identification: It help uncover cybersecurity blind spots before cybercriminals exploit them.
- Security posture assessment: It help evaluate and optimize your security defenses.
- Communication assessment: It reveal communication gaps that may hinder response to cyberattacks.
- Compliance: Documenting security tabletop exercises is essential for incident readiness in regulated industries.
- Response fluency: Simulated incidents help participants practice actions, speeding up response in a real attack.
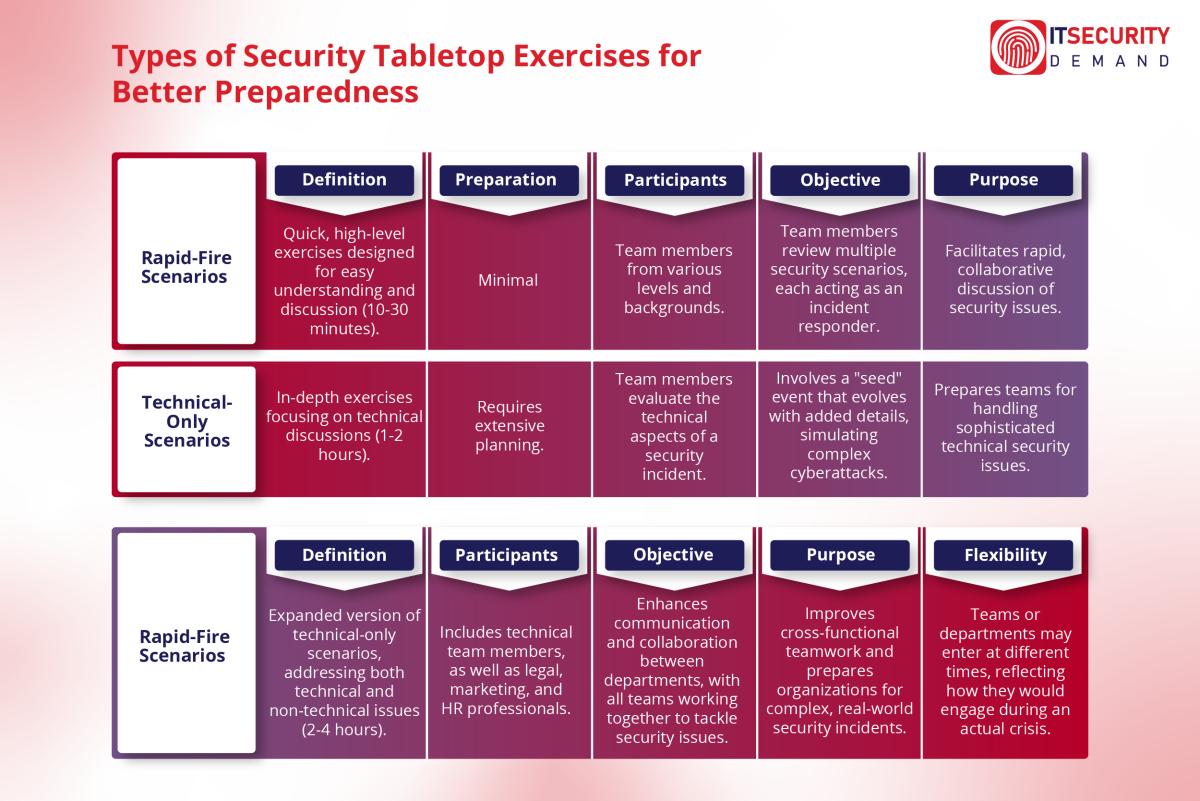
Choosing the Right Security Tabletop Exercises: Which One is Right for Your Organization
Developing a Security Tabletop Exercises: 17 Best Practices
For organizations to effectively create your own security tabletop exercises, consider the following best practices:
-
Know your target audience
Identify who your cybersecurity scenario is crafted for and customize it respectively. For example, a complex scenario is well-suited for testing a cybersecurity team, while a simpler, relevant issue works better for IT or DevOps teams, ensuring participants can fully engage and focus.
-
Select the right participants
Know whether to focus on a single team or include various teams or departments in your security scenario. A single-team approach assists you verify how particular participants reply to a cyberattack, while involving multiple teams fosters collaboration across various business units to tackle the incident efficiently.
-
Confirm when to involve participants
Examine when various teams should be brought in during the cybersecurity scenario. For example, if PII is violated, involve legal team members for compliance.
Involving participants from all departments fosters better cross-functional communication and collaboration.
-
Decide on participant numbers
Assure your scenario includes enough participants to partner effectively. We generally include up to 25 people from different levels or departments. Take into account your organization’s size and team structure when selecting the number of participants.
-
Manage the duration of your exercise
Allot needed time for participants to finish the tabletop exercise. Try to keep sessions concise, as long, drawn-out exercises can make it difficult for participants to adjust their schedules and commit to a session lasting several hours.
-
Prepare your materials
Use tools like PowerPoint to show your scenario, with each slide describing events and questions for participants. Keep your presentations to around 20 slides for tabletop exercises.
-
Create your tabletop scenario
Craft a fictional story and tailor the details depending on the scenario. Including recent news can capture participants’ interest. For more complicated scenarios, incorporate clues in systems and logs for participants to discover and follow.
-
Tailor your exercise to participants
Craft your cybersecurity exercise depending on the participants’ security knowledge. A comprehensive scenario suits skilled experts, while a high-level approach may work better for others.
Ensure the narrative feels realistic by gathering insights from key areas within your organization, making it more relatable to your audience.
-
Gather participant feedback
Call participants to share any suggestions for betterment of exercise. They can provide valuable insights into common cybersecurity challenges they face on daily basis.
Use this feedback to make a scenario that assists participants tackle these issues in the future.
-
Outline your scenario
Develop a flow diagram to map out the simulated attack and identify any loopholes. Seek feedback from connected team members to find out issues and ensure the scenario is realistic.
-
Create discussion questions
Highlight any questions that arise while creating your scenario. These questions can be a starting point of the valuable discussions among participants.
-
Review your scenario
Check your scenario several times before demonstrating it. If not sure about timing, it’s better to be alert. Modify the presentation if it goes beyond the available time for participants.
-
Set the tone
Inspire for the full participation from all attendees, irrespective of seniority or tenure. This exercise permits everyone to contribute and boost your security posture. The more communication and collaboration will give greater value for all.
-
Moderate the exercise
Moderation helps keep the exercise on track and on time. The moderator should avoid participating, instead guiding the scenario, allowing time for discussion, and offering prompts and questions when needed.
-
Track issues
Validate someone is recording any issues that come during the exercise. This assist identify difficulties that may affect the performance of your scenario.
-
Monitor time
Set a timer for the exercise and adhere to it. Keep participants focused and remind them to stay on task as the scenario unfolds.
-
Review your results
After the exercise, calculate the results and how they can enhance daily operations. For instance, make a PDF for auditors if the exercise was compliance-based. Permit participants to review findings and repeat the exercise later to check if issues have been solved.
Final Words
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) promotes over 100 Tabletop Exercises (CTEPs) to aid organizations to become ready for various threats. These exercises include:
- Cybersecurity scenarios, such as ransomware, insider threats, phishing, and ICS compromise.
- Physical security scenarios, like active shootings, vehicle-ramming, IEDs, and UAS threats.
- Cyber-physical convergence, addressing threats that combine both cyber and physical components.
Finally, tabletop exercises are necessary for cybersecurity preparedness, assisting organizations better their resilience against cyberattacks.
By utilizing the resources and best practices given, organizations can better protect their operations in newly growing digital world.
Enhance your understanding by delving into various security-related whitepapers accessible through our resource center.